BACK


Product Design: VMware Carbon Black Vulnerability Manager
About: VMware CB Vulnerability Management Datasheet(All content on this page is exclusive property of VMware)
Role: My goal was to design the end-to-end experience of a Vulnerability Management solution for Security Operations teams using Carbon Black to secure their workloads and endpoints.
Tools used: : Figma
Collaborated with: : Product managers, UI dev, IT team, users
Key Product Requirements:
- Organizations want an frictionless and intuitive solution to harden their security posture by proactively monitoring vulnerabilities and its impact on the users' workloads
- Users need a simplified and contextual interface that overcomes issues in complex legacy solutions.
- Users have alert fatigue and require risk-prioritized visibility into impact to their environment
Users:
The primary users were the Security team, IT Team and the vulnerability management teams
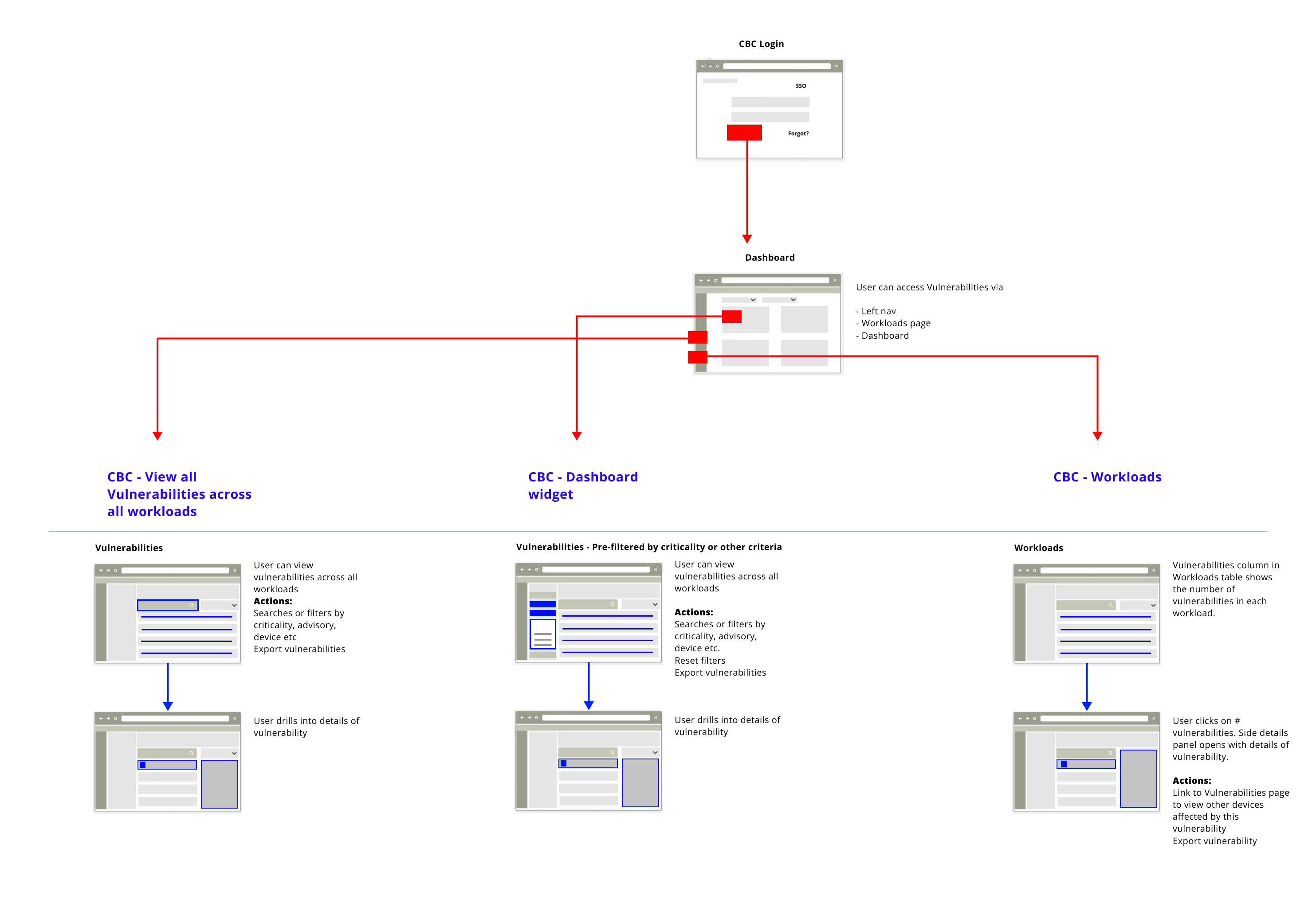
Design phases:
- After the initial product features were identified, I created lo-fidelity wireframes and user journeys. I conducted workshops with key stakeholders, potential users ( internal IT teams) and product managers, to validate some assumptions. This early feedback was extremely crucial in determining the design language.
- Based on several interviews and brainstorming, I got inputs with regards to the challenges faced by vulnerability management teams and used that to shape the product features and workflows. I learned from potential users that while security transparency takes center stage, managing vulnerabilities is a time-consuming and laborious process which had to be solved for. I crafted the product experience using these inputs in hi-fidelity mockups.
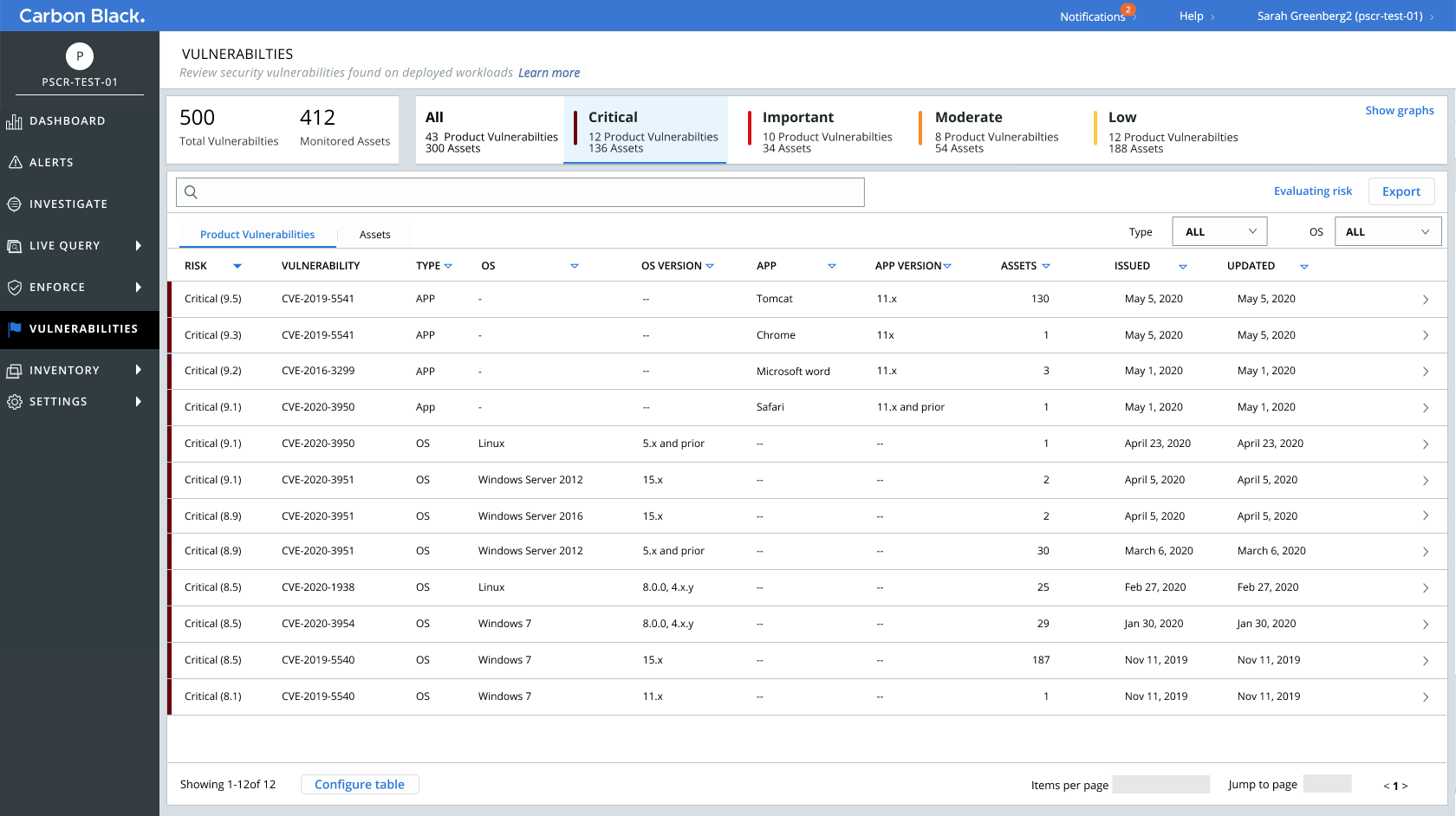
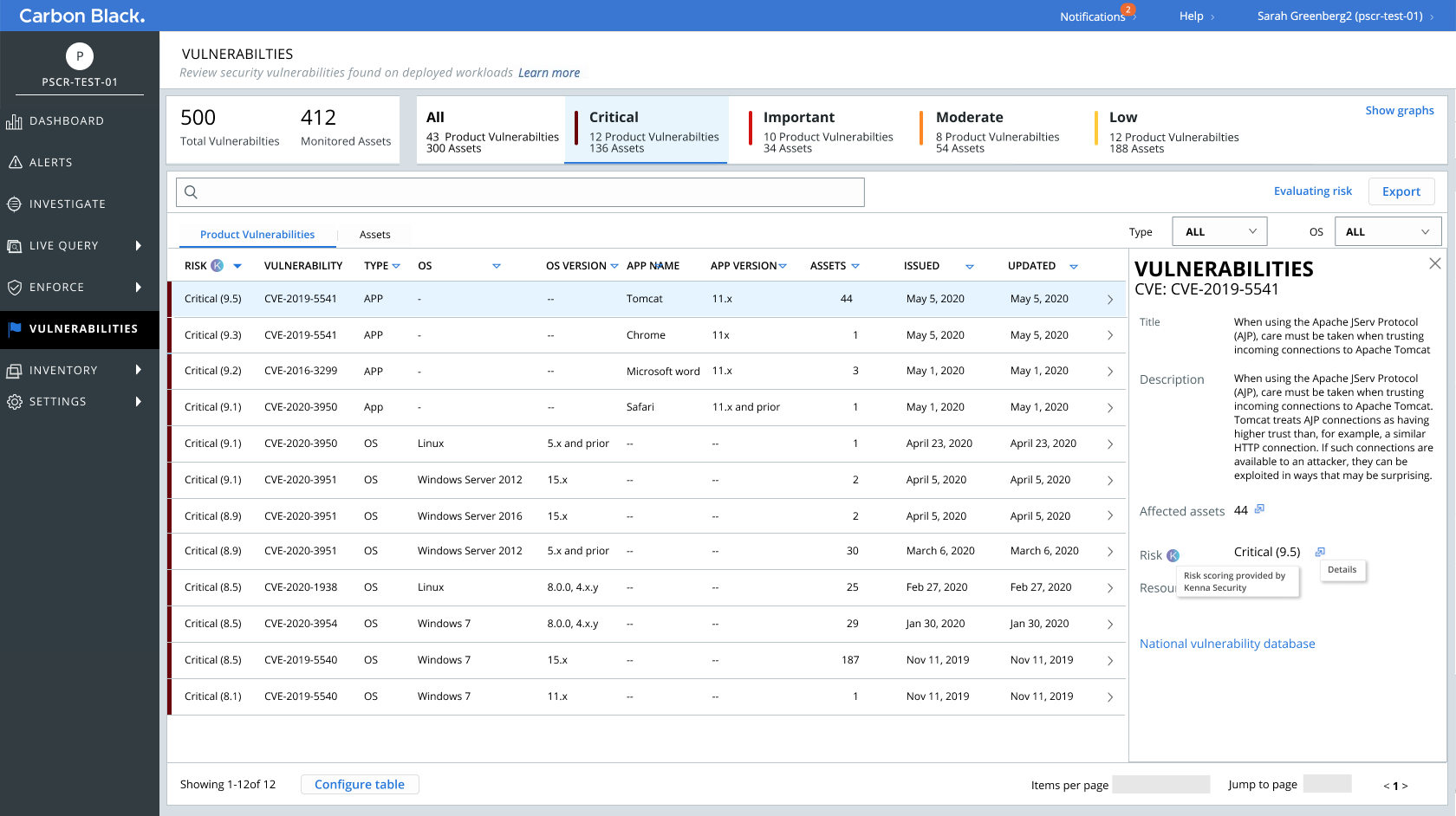
- Armed with the feedback from users, I focused on creating designs that surfaced the most critical vulnerabilities, along with related actions. These designs resulted in a more seamles and risk-prioritzed approach, saving users the time spent in looking for the needle in the haystack
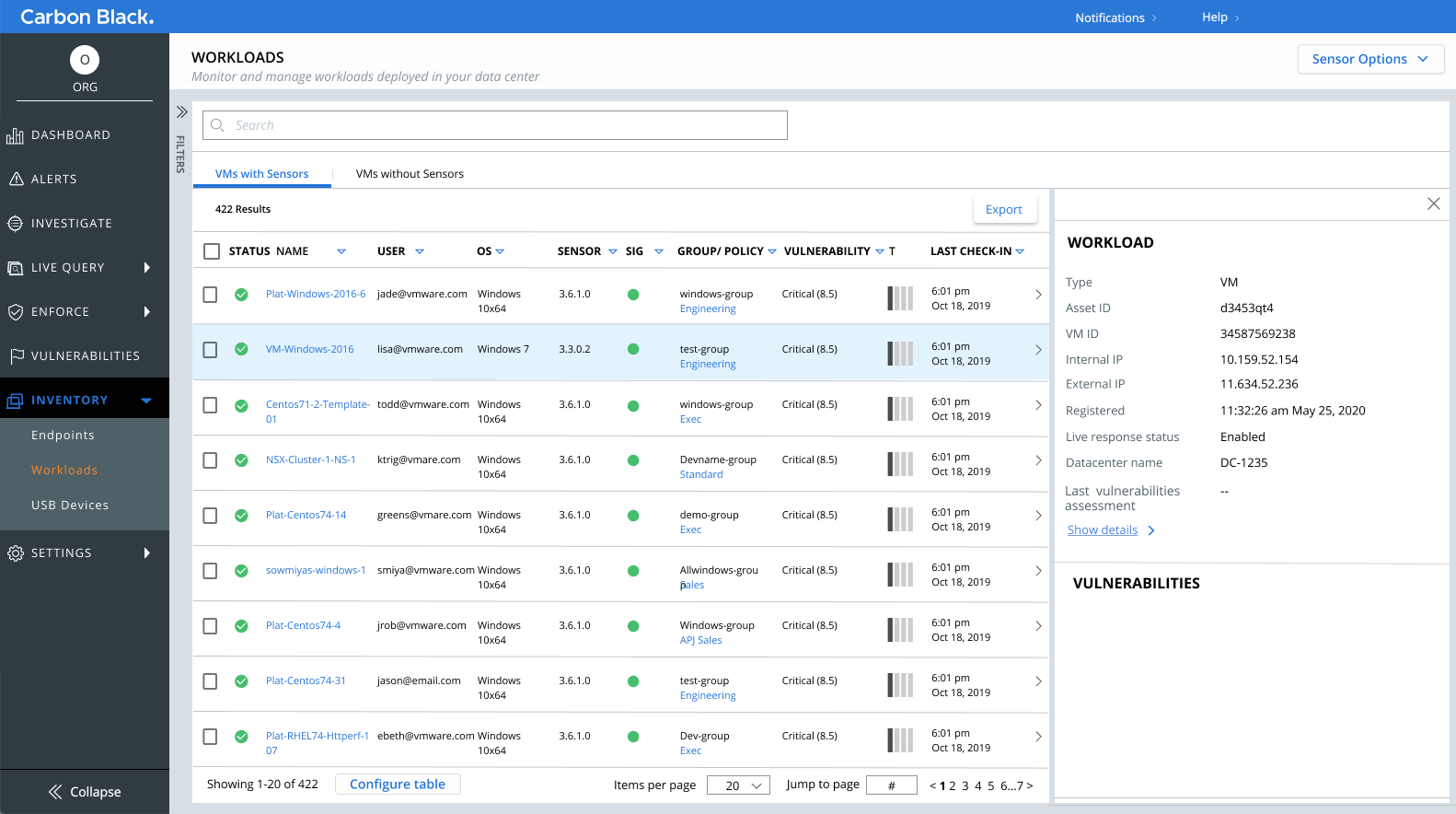
Sample mockups






Outcomes:
- Design aligns with user’s mental model of vulnerability management
- Enables seamless hardening practices
- Consolidates products by offering key security functionality